Active Threat Assessment: Identify Potential, Imminent, and Immediate Threats
Threat assessment means different things to different people. Security professionals, military personnel, psychologists, and school counselors all conduct threat assessment, yet they perform very different tasks.
To law enforcement, security, and military professionals, threat assessment often refers to the process of identifying potential and immediate threats such as active shooters, active assailants, terrorists, or people carrying concealed weapons. These people become a focus for further observation or interdiction. At Second Sight, we call this process active threat assessment.
In this post, we will describe the active threat assessment methodology and explain why a systematic process is necessary.
If you would like to read more about other threat assessment approaches, check out our guides for law enforcement and security professionals.
We encourage any law enforcement, military, or security professionals who have the task of observing and protecting public and private persons or property to become familiar with active threat assessment – it can help keep you safe and more successfully execute your mission.
The Active Threat Assessment Methodology
Active threat assessment requires a focused observation of behaviors and actions. As part of this methodology, you must first systematically assess your environment and determine the pattern of consistent behavior. By systematically assessing your surroundings and environment, you can enhance your situational awareness, which is a critical precursor to decision-making for any first responders.
Once a pattern of consistent behavior is established, it is possible to identify people whose behavior deviates from this pattern. Research shows that behavioral deviations point to potentially suspicious individuals (or person of interests). Importantly, most deviations are not threats, but by looking for clusters of deviations it is possible to identify potential POIs.
A person of interest (POI) is an individual who becomes a target for further investigation due to their suspicious activity, lack of an explainable objective, or display of threatening behavior.
After identifying a POI, you should then assess threat indicators. Threat indicators are verbal or visual behaviors that an individual exhibits when they are being deceptive, threatening, trying to hide in plain sight, or carrying contraband or weapons.
Active threat assessment allows you to filter through a crowd of people, identify who is a potential active threat, and make an informed decision on what to do next. Additional tips on critical decision-making can be found in the Critical Decision-Making Model section of the Police Executive Research Forum’s ICAT (Integrating Communication Assessment and Tactics) training.
Why Is It Hard To ID Active Threats?
Think what you see in the picture below. Why is it hard to identify an active threat at a place like this?
There are four big reasons:
1. Every place has a different pattern of life that is constantly changing, and you need to identify that pattern of life to spot what might be a threat;
2. There are often many people in a location, and it can be hard to figure out which individual or group of individuals to focus on;
3. There is no single behavior that indicates 100% someone is a threat; and
4. You need to identify what threatening behaviors you see, and when you see them.
We want all of this done in a way that protects civil liberties. This is difficult, but a systematic evidence-based approach to active threat assessment can help.
The Pattern of Life
Think about all the places where you work or visit throughout the day – airports, train stations, parks, concerts, sporting events, schools, open-air marketplaces.
People in different locations have different goals and are doing different things. The behavior of people within a given location also varies by the time of day, weather, holidays, and countless other factors.
To spot threats, you need to know the pattern of life at the location you are observing. This pattern involves consistently occurring behavior, patterns of movement, and roles/objectives of those present. The need to establish context to identify criminal behavior has been shown in research.
As an observer looking for active threats, you need to be able to quickly and efficiently assess the pattern of consistent behavior where you are working.
Our active threat assessment methodology can help you do this at any location. In turn, you can identify behavior that stands out or deviates from the norm, leading you to identify a potential threat.
Filtering the Crowd
Sometimes you may observe a small number of people in a park, while other times you may be observing hundreds or thousands at a sporting event.
But you can’t watch 100 people at once. You need to be able to filter potentially threatening individuals or groups of individuals from the larger crowd of people in that location.
In any given location, the vast majority of people with whom you interact are law-abiding and have no intent to cause harm. As part of this filtering process, you must dismiss those who are not a threat and focus your attention on the biggest potential threat.
Through systematic observation and the assessment of patterns of consistent behavior, you can filter the crowd and pick out that potential threat. Importantly, psychological visual search research shows that when operational personnel apply a consistent and systematic process to their work, accuracy and hit rates tend to improve.
Identifying Clusters of Behavior
Other than some very obvious visual cues such as a bomb, a weapon, or being caught “red-handed” in the commission of a crime, there is generally no single behavior that signifies a threat.
Even seeing a weapon may not be enough, as some jurisdictions allow legal carrying of firearms. There have been too many stories of off-duty police officers carrying a gun who get shot by other officers by mistake.
Research suggests that it is not one behavior, but clusters of specific threatening behaviors that can help you identify an active threat.
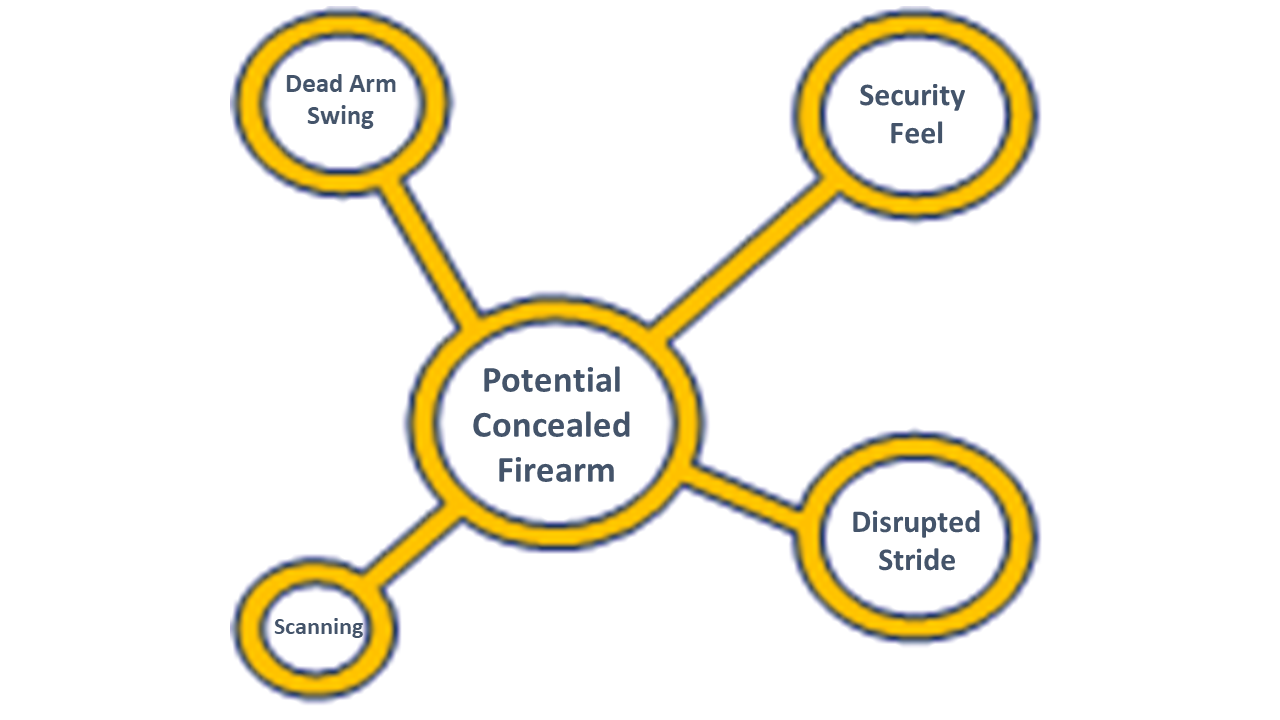
For example, someone touching their waist alone is not enough to tell us they may have a firearm. However, an individual who exhibits multiple threat indicators in combination is a concern. For example, if an individual is repeatedly touching their waist (a security feel), has a dead arm swing, has a disrupted stride when walking, and is constantly scanning the area, it strongly suggests that they are carrying a concealed firearm tucked into their waistband. For more detail on these particular indicators, see our post about concealed weapons at protests.
Learning how to tell if an individual is carrying a concealed weapon is a critical skill that can be used in many situations. In particular, it can help you respond to active shooter situations, which have become all too common in recent years. To learn more about how threat assessment can help you respond to an active shooter, see our post on active shooter prevention.
Unfamiliar with these terms? You can read more about these behaviors in our recent blog post about active threat assessment vocabulary or take one of our training courses.
Through active threat assessment, you can learn to identify clusters of behavior. By looking for clusters of behaviors, you can also more easily dismiss people that are innocuous or non-threatening, allowing you to refocus on the true threat.
When Matters
Certain behaviors are more meaningful based on when they occur. Behaviors may indicate a threat in one situation yet be innocuous in another. Research consistently finds a person’s behavior will be affected by changes in the environment; this is known as the Hawthorne Effect.
Active threat assessment must involve observation over time and the ability to identify changes in behavior based on how a POI reacts to perceived threats. In this way, decision-making can be thought of as a dynamic process, one that often occurs in rapidly evolving situations with intense time pressure.
if we know that people will also react to the presence of perceived threats, then you need to take into account that a person involved in wrongdoing may see a security guard or police officer in uniform as a threat. Therefore, you need to not only assess behavioral indicators and when they occur but also how a person is behaving when interacting with what they may see as a threat.
Certain behaviors are more meaningful based on when they occur. An assessment of an active threat must involve observation over time and identify changes in behavior based on the reaction of that subject to perceived threats.
A Foundation for Active Threat Assessment
Experienced law enforcement, military, and security personnel have engaged in active threat assessment for years. Practitioners who interact with threatening individuals learn to assess threatening behavior and differentiate that threat from that crowd. Maybe you have learned to do this too.
Sometimes this is done consciously, meaning you knew what suspicious behaviors to look for. In other cases, maybe something “just didn’t look right” but you couldn’t explain why.
This subconscious ability to identify things that don’t look right has been described as Intuitive Policing and is supported by researchers and practitioners.
Most learn to identify active threats through on-the-job training (OJT). Most officers learn to identify active threats through on-the-job training (OJT). Generally, the various methods developed have not been standardized and formally taught. It may have been passed along through narratives or instructions from a field training officer to a trainee.
Thankfully, there is some research that can serve as a basis for active threat assessment. For a detailed review of the research on behavioral indicators of violent acts, check out this report from the RAND corporation’s National Defense Research Institute.
Behavioral Criminal Profiling
Criminal behavioral profiling is one tactic related to threat assessment that involves identifying the behavioral tendencies based on the characteristics of a crime. Research indicates criminal behavioral profiling can facilitate better identification of offenders, but it should not involve a sole focus on the age, gender, race, or ethnicity of a subject.
The JDLR Project
Another basis for active threat assessment is the JDLR Project funded by the U.S. Department of Defense. The goal of the JDLR Project was to identify and articulate behavioral indicators associated with threat, fear of detection, or the carrying of concealed weapons.
The project aimed to transfer this knowledge from more experienced to less experienced military personnel and better prepare them for complex environments around the world. These indicators were derived from law enforcement methods to identify persons carrying guns or others involved in suspicious or illicit activities. This research was focused on identifying the visual behaviors associated with specific criminal activities (e.g., carrying of concealed handguns or illegal drugs, smuggling of money and other contraband through airports).
Active Threat Assessment Training
Active threat assessment can help you assess clusters of behavior, dismiss people that are harmless, and focus on people that require immediate attention. This is essential at all times, but especially in rapidly evolving scenarios. Research suggests that following a specified model to guide response in these types of tense situations can result in quick and effective decision-making while reducing mental fatigue.
Would you like learn active threat assessment? We can help through our various online or instructor-led offerings.
Our online IADLEST NCP Certified online Threat Awareness for Law Enforcement and our Threat Awareness for Security Professionals course are available now. Second Sight is also a Preferred CPE Provider from ASIS International. We also have shorter courses for anyone who wants to learn to be more aware of their environment.
-
Akinci, C., & Sadler-Smith, E. (2014). Enacting intuitions: How police use their intuitive judgments in first-response. In Academy of Management Proceedings, 2014(1), 14192. Briarcliff Manor, NY: Academy of Management. Retrieved May 2022 from https://journals.aom.org/doi/abs/10.5465/ambpp.2014.14192abstract
Banks, A. P., Gamblin, D. M., & Hutchinson, H. (2020). Training fast and frugal heuristics in military decision making. Applied Cognitive Psychology, 34(3), 699-709. Retrieved May 2022 from https://onlinelibrary.wiley.com/doi/full/10.1002/acp.3658
Cloud, M. (1985). Search and seizure by the numbers: The drug courier profile and judicial review of investigative formulas. Boston University Law Review, 65, 843–922. Retrieved May 2022 from https://law.emory.edu/_includes/documents/sections/faculty-and-scholarship/articles/cloud/1985-Search-and-Seizure-by-the-Numbers.pdf
Davis, P. K., Perry, W. L., Brown, R. A., Yeung, D., Roshan, P., & Voorhies, P. (2013). Using behavioral indicators to help detect potential violent acts: A review of the science base. The RAND Corporation. https://www.rand.org/content/dam/rand/pubs/research_reports/RR200/RR215/RAND_RR215.pdf
Federal Bureau of Investigation (FBI). (2021). Active shooter incidents in the United States in 2020. Washington, D.C.: Federal Bureau of Investigation, Department of Justice. Retrieved May 2022 from https://www.fbi.gov/file-repository/active-shooter-incidents-in-the-us-2020-070121.pdf/view
Harman, J. L., Zhang, D., & Greening, S. G. (2019). Basic processes in dynamic decision making: How experimental findings about risk, uncertainty, and emotion can contribute to police decision making. Frontiers in Psychology, 10, 2140. Retrieved May 2022 from https://www.frontiersin.org/articles/10.3389/fpsyg.2019.02140/fullJohnson, R. R. (2017). Show me your hands! Police and public perceptions of violent interpersonal cues. Journal of Police and Criminal Psychology, 32(4), 289-299. Retrieved May 2022 from https://link.springer.com/article/10.1007/s11896-016-9221-x
Johnson, R. R., & Morgan, M. A. (2013). Suspicion formation among police officers: An international literature review. Criminal Justice Studies, 26(1), 99-114. Retrieved May 2022 from https://www.tandfonline.com/doi/abs/10.1080/1478601X.2012.705784?journalCode=gjup20
Kahn, K. B., McMahon, J. M., & Stewart, G. (2018). Misinterpreting danger? Stereotype threat, pre-attack indicators, and police-citizen interactions. Journal of police and criminal psychology, 33(1), 45-54. Retrieved May 2022 from https://link.springer.com/article/10.1007/s11896-017-9233-1
Kocsis, R. (2006). Criminal Profiling. Humana Press. Retrieved May 2022 from https://link.springer.com/book/10.1007%2F978-1-59745-109-3.
Kocsis, R. N., Middledorp, J., & Karpin, A. (2008). Taking stock of accuracy in criminal profiling: The theoretical quandary for investigative psychology. Journal of Forensic Psychology Practice, 8, 244-261. Retrieved May 2022 from https://www.tandfonline.com/doi/abs/10.1080/15228930802282006
Luke, T. J., Hartwig, M., Joseph, E., Brimbal, L., Chan, G., Dawson, E., ... & Granhag, P. A. (2016). Training in the strategic use of evidence technique: Improving deception detection accuracy of American law enforcement officers. Journal of Police and Criminal Psychology, 31(4), 270-278. Retrieved May 2022 from https://link.springer.com/article/10.1007/s11896-015-9187-0
McCambridge, J., Witton, J., & Elbourne, D. R. (2014). Systematic review of the Hawthorne effect: New concepts are needed to study research participation effects. Journal of Clinical Epidemiology, 67(3), 267–277. http://doi.org/10.1016/j.jclinepi.2013.08.015.
Meehan, N. (2018). Threat assessment training for peacekeepers: A proven business approach. Small Wars Journal. Retrieved May 2022 from https://smallwarsjournal.com/jrnl/art/threat-assessment-training-peacekeepers-proven-business-approach
Meehan, N. and C. Strange. (2015). Behavioral indicators of legal and illegal gun carrying. Memorandum Report - NRL/MN/5508--15-9597. United States Naval Research Laboratory. Retrieved May 2022 from https://apps.dtic.mil/sti/pdfs/ADA620183.pdf
Meehan, N. and McClary, M.(2015). Behavioral indicators of drug Carriers in open spaces. Memorandum Report - NRL/MN/5508--15-9596. United States Naval Research Laboratory. Retrieved May 2022 from https://apps.dtic.mil/sti/pdfs/ADA620184.pdf
Meehan, N., McClary, M., and C. Strange. (2015). Behavioral indicators of drug couriers in airports. Memorandum Report - NRL/MN/5508--15-9595. United States Naval Research Laboratory. Retrieved May 2022 from https://apps.dtic.mil/sti/pdfs/ADA620185.pdf
Moria, K., Albu, A. B., & Wu, K. (2016, June). Computer vision-based detection of violent individual actions witnessed by crowds. In 2016 13th Conference on Computer and Robot Vision (CRV), 303-310. IEEE. Retrieved May 2022 from https://ieeexplore.ieee.org/abstract/document/7801536
Penney, G., Launder, D., Cuthbertson, J., & Thompson, M. B. (2022). Threat assessment, sense making, and critical decision-making in police, military, ambulance, and fire services. Cognition, Technology & Work, 1-17. Retrieved May 2022 from https://link.springer.com/article/10.1007/s10111-022-00694-3
Perona, M., Rahman, M. A., & O'Meara, P. (2019). Paramedic judgement, decision-making and cognitive processing: a review of the literature. Australasian Journal of Paramedicine, 16. Retrieved May 2022 from https://ajp.paramedics.org/index.php/ajp/article/view/586
Pinazzatto, A. J., Davis, E., C. Miller (2004). Intuitive policing: Emotional/rational decision-making in law enforcement. F.B.I. Law Enforcement Bulletin, 1. Retrieved May 2022 from https://leb.fbi.gov/file-repository/archives/feb04leb.pdf
Police Executive Research Forum (PERF). (2016). ICAT Module #2: Critical decision-making model. Washington, DC: Police Executive Research Forum. Retrieved May 2022 from https://www.policeforum.org/assets/ICAT/module%202_cdm_dec16.pdf
Reid Meloy, J., Hoffmann, J., Guldimann, A., & James, D. (2012). The role of warning behaviors in threat assessment: An exploration and suggested typology. Behavioral Sciences & the Law, 30(3), 256-279. Retrieved May 2022 from https://onlinelibrary.wiley.com/doi/abs/10.1002/bsl.999
Schuurman, B., & Eijkman, Q. (2015). Indicators of terrorist intent and capability: Tools for threat assessment. Dynamics of Asymmetric Conflict, 8(3), 215-231. Retrieved May 2022 from https://www.tandfonline.com/doi/abs/10.1080/17467586.2015.1040426
Spain, R., Hedge J., & Blanchard, J., (2017). Examining predictors of visual search success in transportation security officers and behavior detection officers. Proceedings of the Human Factors and Ergonomics Society Annual Meeting. 61(1), 1308-1312. Retrieved May 2022 from https://doi.org/10.1177/1541931213601809
Sweet, D. M., & Burzette, R. G. (2018). Development of the nonverbal cues of interpersonal violence inventory: Law enforcement officers’ perceptions of nonverbal behavior and violence. Criminal Justice and Behavior, 45(4), 519-540. Retrieved May 2022 from https://journals.sagepub.com/doi/10.1177/0093854817753019
Woodhams, J., Hollin, C. R., & Bull, R. (2007). The psychology of linking crimes: A review of the evidence. Legal and Criminological Psychology, 12(2), 233-249. Retrieved May 2022 from https://bpspsychub.onlinelibrary.wiley.com/doi/abs/10.1348/135532506X118631